Official Supplier
As official and authorized distributors, we supply you with legitimate licenses directly from 200+ software publishers.
See all our Brands.
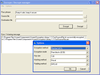
Screenshots: An Encryption Method object represents a particular encryption algorithm offered by the library. ... Objects of this type are assigned to the Xceed Encryption control's EncryptionMethod property ... in order to specify the underlying encryption method to use. ... Read more Show more results from this product
Screenshots: The Hashing Method object represents a particular hashing algorithm offered by the library. Objects of this type are assigned to the Xceed Hashing control's HashingMethod property in order to determine the hashing algorithm to use when calling Xceed Hashing control methods that hash data. ... Read more
Screenshots: Encrypting and decrypting entirely in memory requires five steps; Specify the encryption method ... to use; Specify the Secret Key to use; Tell the library to encrypt; Obtain the encrypted data and Make ... Read more

Screenshots: 0 ... Read more
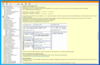
Screenshots: The manual explains in detail the important points on how to encrypt, and which mistakes to avoid. ... Read more Show more results from this product
Screenshots: The XOR.-Command does far more than XOR and contains parts of the highly optimized encryption ... Read more
Screenshots: and helps you to find out if and how well they might be encrypted. 0 ... Read more
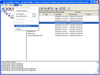
Screenshots: Import an encryption key to use for added security across networks. ... Read more
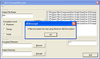
Screenshots: Perform AES encryption and decryption on files. ... Read more
Screenshots: SQL Server backups. You can also encrypt your backup files using 128- or 256-bit key Advanced ... Encryption Standard encryption. ... Read more Show more results from this product
Screenshots: the passwords for encrypted backups. Step 2: Specify the database to which you want to restore the backups. Step ... Read more
Screenshots: PowerTCP SSH and SFTP for.NET includes encryption/decryption using Triple DES and AES. ... Read more
Screenshots: The PDF Secuity tab holds all PDF security settings including file encryption, file permissions ... Read more
Screenshots: The PDF Secuity tab holds all PDF security settings including file encryption, file permissions ... Read more
Screenshots: Get aware of waiting blocks due to Network I/O (capture even encrypted data). 0 ... Read more